I figured I would blog about how to adjust CyberArk’s marketplace Cisco SSH CPM plugin to utilize a domain account as the logon, enable, and reconcile account, instead of local accounts it is set to use by default. Utilizing a domain account allows for ease of password management of local accounts across appliances. Ensure you rotate the domain service account often.
Please try these items in your QA lab (and QA Cisco appliances) before deploying to production. I’m not responsible for your own actions, including performing these in your company or your own environment.
Prerequisites —
- CyberArk Cisco Router SSH CPM Plugin (Uses latest TPC plugin), found here — https://cyberark-customers.force.com/mplace/s/#a3550000000EiAUAA0-a3950000000jjSpAAI. This works for Cisco Routers, Switches, and Wireless Controllers.
- Access to download the CPM plugin from CyberArk marketplace
- RDP access to your CPM server(s)
- Admin access to your PVWA site
- Safe and accounts added in your vault
- Domain service account configured with Cisco appliance authentication and authorization integration (Cisco TACACS+).
- Domain service account configured to be logon account, enable account, and reconcile account for the local cisco accounts we’ll be managing.
- Domain service account managed by a windows domain platform policy for rotations.
- Target Cisco local accounts set with the Cisco entity type of “ciscouser” in PVWA.
Let’s go —
- Extract the Cisco plugin zip file from the CyberArk marketplace.
- Open the ciscoprocess.ini file to update.
- Throughout the ciscoprocess.ini file, look for “<extrapass2\address>” and “<extrapass2\port>”. These links refer to the domain account’s domain address, and wouldn’t even have a port field set. Update these to be <address>, and <port>. This updates the plugin to utilize the target account’s address and port fields. DO NOT change the <extrapass2\username> items.
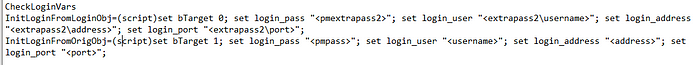
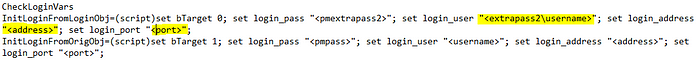
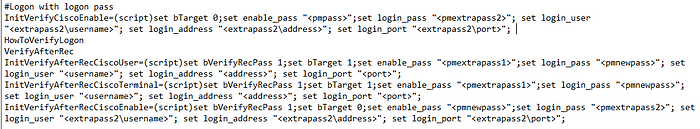
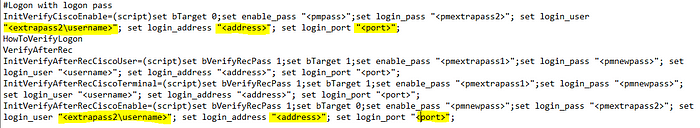
4. Also, through the ciscoprocess.ini file, look for <extrapass3\address>” and “<extrapass3\port>”. Update these as well to be <address>, and <port>. DO NOT change the <extrapass3\username> items.
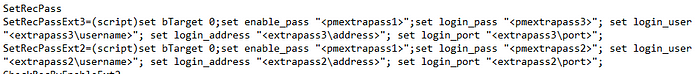
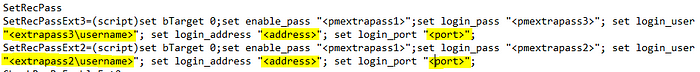
5. Save the file. Save the name of the existing zip file. Delete the existing previously downloaded zip file.
6. Select all files within the folder and create another zip file with the same zip name.
7. Log into your PVWA site. Import the plugin into your PVWA site. Admin>Platform Management>import platform
8. If the platform already exists, you can duplicate the OOB one, append the name with — OOB. Delete the existing platform, then try importing the plugin again.
9. Duplicate the “Cisco Router” plugin to utilize your own company’s naming scheme. For example, <Company name>CiscoSSH.
10. Now RDP into your assigned CPM server for this plugin’s use.
11. Navigate to your CPM server’s CyberArk Password Manager>Bin> folder.
12. Open the ciscoprocess.ini file. Make sure your changed ini file propagated.
13. Restart the CPM service.
14. Log out of the CPM server
15. Going back to your PVWA site, pull up your target Cisco SSH accounts.
16. Assuming your domain service account password is set and linked to the target local accounts, kick off a password reconciliation for your target Cisco account. Wait for the “immediate” update. Sorry, CyberArk dry humor as “immediate” to them means within 5 minutes (set as default by platform policy).
17. Boom.

Additional items to think about —
- How often will you have the domain service account rotate — daily?
- Work with your Network Engineers to assist with their side of the configurations required on the Cisco appliances (routers, switches, WLS controllers).
- There’s a newer password change command which is used, that the CPM plugin can be adjusted to utilize as well. Adjust the “ChangeUserPass=username <username> password <pmnewpass>” line to be the newer password change method as desired. Obviously test this in your QA lab. Ask your network engineer resource what CLI password change text is used and/or should be changed to.
- You could rename the process and prompts ini files to be a custom name and update your platform references to the new names if you like. That would allow you to recognize that they’re custom for your org. This will help you in upgrades down the line. Be sure to update the platform referenced names if you do this.
Looking for a partner in your Privileged Access Management rollout?
Check out my site here — https://www.keyvaultsolutions.com/pages/contact-us
