Here’s an overview of how to configure CyberArk’s PVWA for 2FA with PKI and LDAP authentication. This is the “poor mans” version of 2FA as most modern implementations utilize newer, better methods, such as SAML, WebAuthn, OIDC, etc. tied to your business’ identity provider. Only go this route if you have no other option, and/or lack funding to implement the better alternatives noted above. After reading this, you can check out my recent “CyberArk PVWA integration with SAASPASS SAML authentication” blog.
This blog is a combination of multiple sources, including CyberArk documentation and other helpful Security Engineers in the CyberArk community.
Don’t test in Production. Use a lab environment and related lab accounts and such to validate these configurations. I’m not responsible for your actions. I’m using test accounts and such to illustrate how to configure the pieces required.
Prerequisites —
- LDAP/S integration with your vault is already configured, with vault admin groups already mapped and permissioned correctly
- CyberArk PVWA installed and configured in your environment
- RDP access to your PVWA server(s)
- Admin access to your Password Vault Web Access (PVWA) site
- Vaulted Admin Account(s) you want to utilize with PKI+LDAP/S authentication. This can be your privileged domain user accounts for example.
- Personal Client Certificate(s) created for your admin account(s) that have your Active Directory domain trust chain pieces included.
- PVWA IIS Certificate for server and/or your VIP already loaded.
Configure your PVWA servers for PKI—
- RDP into your PVWA server
- Backup your applicationHost.config file under c:\Windows\System32\InetSrv\Config\ .
- Update the applicationHost.config file to add this at the end of the file. Save the file. See below for an example.
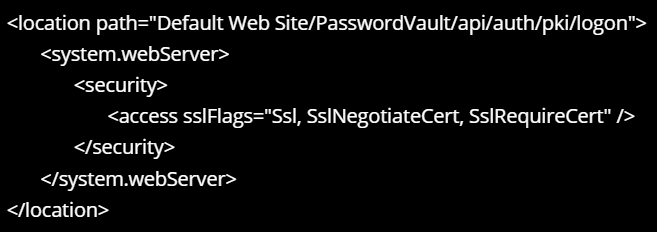
- Open CMD as admin. Run iisreset to recycle IIS.
- Repeat for each PVWA server you have, or copy/paste the files onto any other PVWA servers you have and perform an IIS reset on those too.
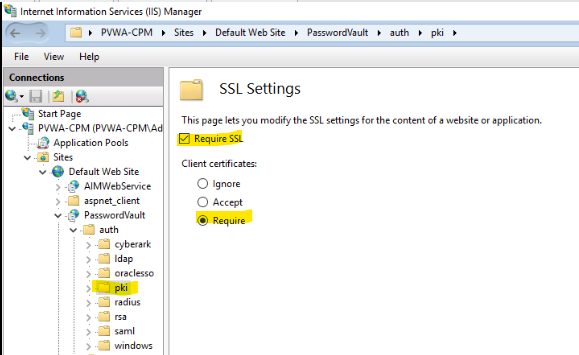
- Additionally, within IIS Manager for your PVWA site’s PasswordVault/auth/pki subfolder, open SSL Settings.
- Ensure your PVWA IIS pki folder is set to Require SSL and for client certificates, Required is set. Repeat for each PVWA server you have.
Within PVWA Website Administration — Configure PKI + LDAP/S Authentication —
- Open your PVWA server site (for example, https://pvwa-cpm.acme.com/PasswordVault/) . Login as an administrator account.
- Click Administration > Options.
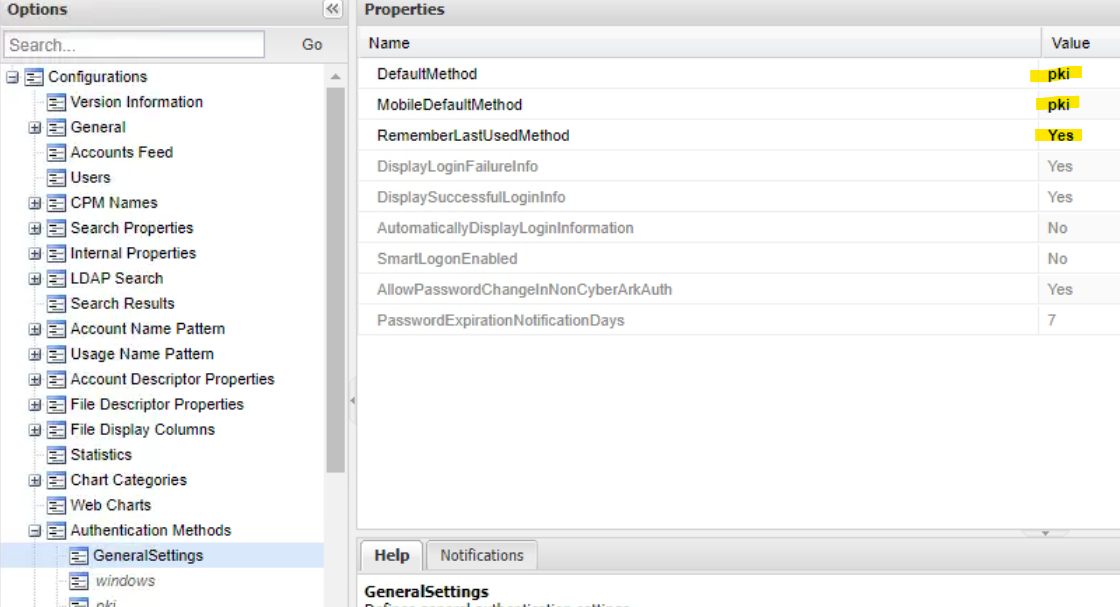
- Click Authentication Methods> GeneralSettings.
- Set Default Method to pki.
- Set MobileDefaultMethod to pki.
- Set RememberLastUsedMethod to Yes.
- Click Apply.
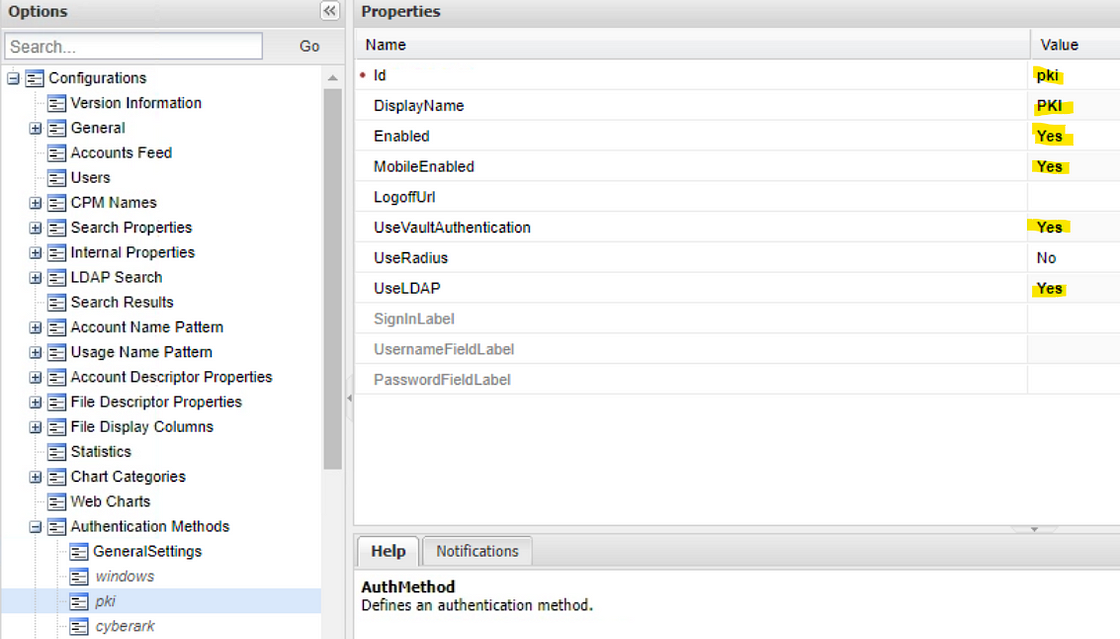
- Under Authentication Methods. Select pki.
- Set Enabled to Yes.
- Set DisplayName to PKI.
- Set MobileEnabled to Yes.
- Set UseVaultAuthentication to Yes.
- Set Use LDAP to Yes.
- Click Apply.
- Under Configurations>Click General.
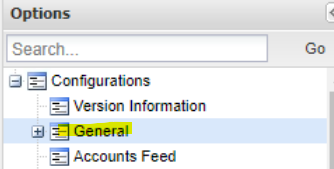
- Set ValidatePKICertificate to Yes.
- Click Apply.
Try PKI + LDAP/S Authentication on your PVWA server —
- Open your PVWA server site using PKI (for example, https://pvwa-cpm.acme.com/PasswordVault/v10/logon/pki)
- Select your personal certificate to utilize for PKI auth, hit ok.
- If your pki certificate was accepted successfully, it redirects you to the LDAP login page for your related ldap username.
- Log in using your ldap username and password.
- Confirm that any other admin admins on your team are able to login using the new PKI + LDAP/S method.
Disable standalone LDAP Authentication within PVWA Website Administration —
- You may be thinking at this point, ok great, we’re done! Nope! Why are we doing this step? Why does it matter? It matters because if we don’t disable standalone LDAP access to logon to PVWA, users can still continue to utilize single factor LDAP authentication, which fails the requirement of only allowing Admin logons with 2FA to the PVWA site.
- IMPORTANT — ENSURE that before you do this step that you have a backup method to log into your vault incase the authentications don’t work as expected. For example, a break-glass admin account configured with CyberArk authentication. Re-confirm that other admin admins on your team are able to login using the new PKI + LDAP/S method you configured above with their own personal certificates.
- Open your PVWA server site (for example, https://pvwa-cpm.acme.com/PasswordVault/) . Login as an administrator account.
- Click Administration > Options.
- Click Authentication Methods> ldap.
- Set Enabled to No.
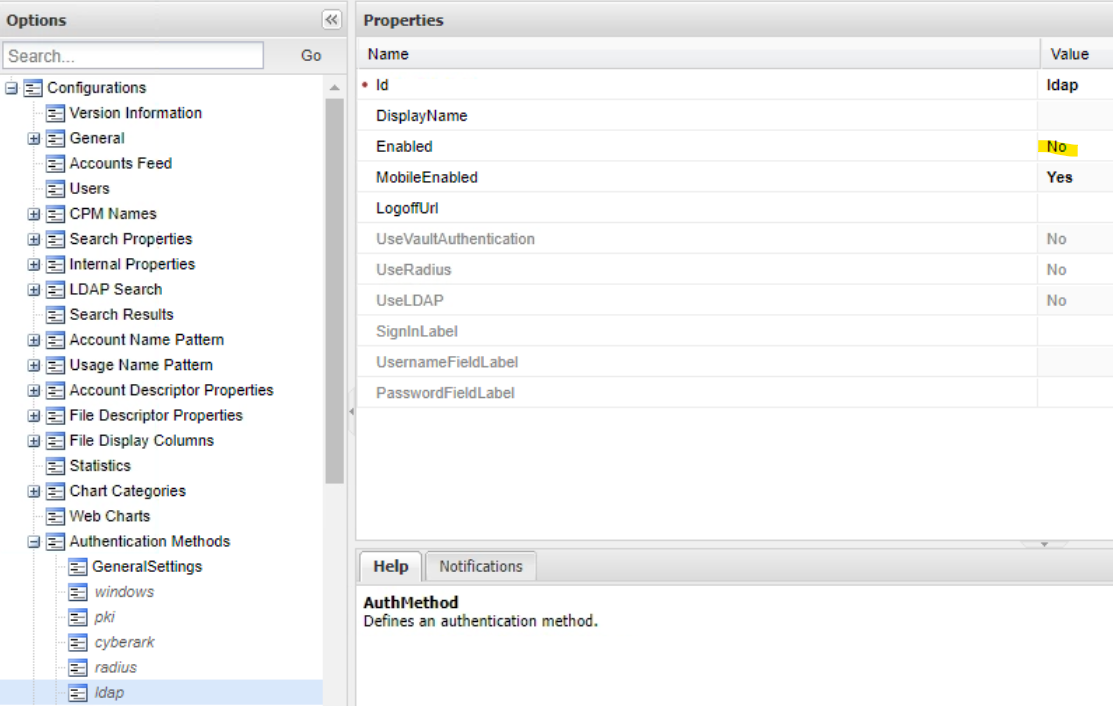
- Click Apply.

Looking for a partner in your Privileged Access Management rollout?
Check out my site here — https://www.keyvaultsolutions.com/pages/contact-us
Recommended items:
- Have separate vaults for Prod and Non-Prod.
- Disable standalone LDAP authentication as shown above if you only want users to utilize 2FA pki + LDAP/S for authentications.
- Document your integration.
- Improve your 2FA authentication by utilizing SAML authentication with SAASPASS or similar. My related blog detailing those steps: https://medium.com/@aglerj/cyberark-pvwa-integration-with-saaspass-saml-authentication-581f5434cf35
- Back up your configuration files after everything is successful within Github, and/or within a CyberArk Vault safe such as VaultInternal or similar.
Related CyberArk Documentation—
- https://docs.cyberark.com/PAS/13.0/en/Content/PAS%20INST/PKI-Authentication-Personal-Certificate.htm
- https://cyberark.my.site.com/s/question/0D52J00007ZGBE6SAP/implement-2-factor-authentication-using-pkildaps
- https://www.reddit.com/r/CyberARk/comments/ica7ev/has_anyone_enabled_2fa_with_pki_ldap_how_does/
- https://docs.cyberark.com/PAS/12.6/en/Content/Landing%20Pages/LPLDAPIntegration.htm?tocpath=Administrator%7CUser%20Management%7CTransparent%20user%20management%20using%20LDAP%7C_____2
- https://medium.com/@aglerj/cyberark-pvwa-integration-with-saaspass-saml-authentication-581f5434cf35
